Submitted by Rewin Koul on 25/Sep/2012 10:36
Greetings beginners. Hopefully in the next 5-10 minutes that you are going to give
to this article, you will be learning the basic security features of Internet Explorer
(IE).
To start with, if you want to be completely secure, free from all kinds of threats; the only solution available is to never buy a computer. But you probably already own a computer, so the next option can be to bury it 8 feet under the ground. No other safety measure you take can assure 100% security to you or your online communications. But then, who needs 100% security? Almost all the people using the internet are not preplanned victims, but gullible innocent web browsers that fall prey to shrewd hackers.
To safeguard you from this, almost all the web browsers provide you with some basic security features that you should be aware of while going online, because your privacy is important to you. Here, we discuss about IE, although most of these features are same/similar in all browsers, some browsers support extra features for better security options.
Now, taking IE in perspective let us talk a bit about its essential features which set it apart from other browsers. IE truly provides a hugely rich set of security features that can be configured. Microsoft defines security “zones” such as "Internet," "Local intranet," "Trusted sites," and "Restricted sites." Although each of these categories is fairly loose, each can be finely tuned to suit the user’s needs.?
?In fact, the level of tuning options in IE is almost daunting. Other browsers, say Firefox, which has a powerful but simplistic set of choices. It follows the all- or-nothing principle. Either it can be followed or not, for every site. IE makes it easy to make separate zones for particular websites such that even a lay-man can place sites into the zones based on how much trust it has on the respective website. These settings at first do limit the functionalities for websites that are not added to the “secure zones” and may seem irritating to the user at first, but intrinsically they save us from all scripting attacks and unwanted pop-ups etc. are not displayed on sites that are not in the secure zones.
How to change zones’ settings in IE :
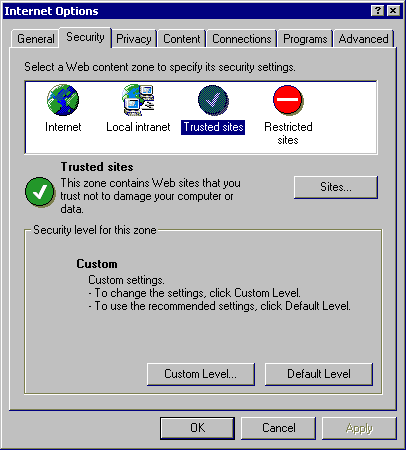
In Internet Explorer, select the "Tools" menu, then "Internet Options". Select the "Security" tab. This will bring up the screen shown to the right. To modify one of the four security "zones", click on the zone's icon, then click the "Custom Level" button.
How to add sites to the secure zone :
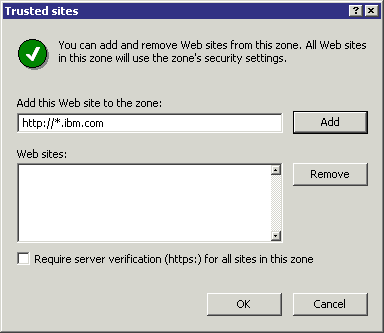
To add a site to the "Secure Zone", click on the "Secure Zone" icon in the "Security" tab, then select the "Sites" button. The screen shown on the right will be displayed. Enter the name of the site to add, (including the "http://" bit), then click the "Add" button.
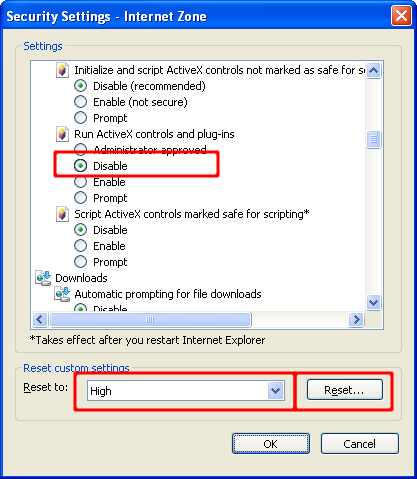
For more control over what features are allowed in the zone, click the Custom Level button. Here you can control the specific security options that apply to the current zone. For example ActiveX can be disabled by selecting Disable for Run ActiveX controls and plug-ins. Default values for the High security setting can be selected by choosing High and clicking the Reset button to apply the changes.
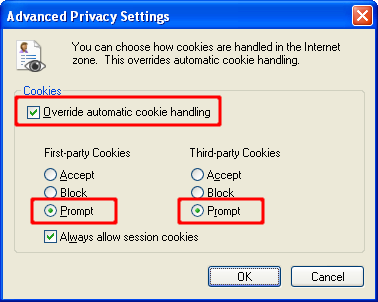
The Privacy tab contains settings for cookies. Cookies are files placed on your computer by various sites that you visit either directly (first-party) or indirectly (third-party). A cookie can contain any type of data. It is often used to track your computer as you move through a web site and store valuable information. I recommend that you select the “Advanced” button and select “Override automatic cookie handling”. Then select Prompt for both first and third-party cookies. This will prompt you each time a site tries to place a cookie on your machine. Also, if the number of cookie prompts are too many and unbearable, the option to “Always allow session cookies” can be enabled.
I would like to mention some other very basic points that would help keep you safe “online”. Be careful only on the pages where you fill some kind of form thereby providing the host with some of your credentials. That is where the hacker actually beats you to collect your information. The most common practice that hackers adopt is to make a ‘Phishing Page’. A phishing page is a web page that looks exactly like a trusted website and sometimes even performs the exactly same desired functionality. It is relatively very easy to detect a phishing page, in case you ever land on one. Always while typing in personal information, take care of the web address, the url. The url can be long and complex and twisted, but it should always start with a fixed format i.e. “www.xyz.com”. Here, “xyz” is the name of the site. This is often modified as www.ab.xyz.com or something similar. What you need to keep in mind is that the word preceding “.com” should be the actual name of the site you need to visit. IE has a built in feature of Domain Highlighting wherein this true name of the website is highlighted in black and the rest is shown in grey. So, its pretty easy to identify a fake page.
Also, IE has Cross site scripting (XSS) filter, which can help prevent attacks from phishing and fraudulent websites that might attempt to steal your personal and financial information. Plus, a 128-bit secure (SSL) connection for using secure websites. This helps Internet Explorer create an encrypted connection with websites run by banks, online stores, medical sites, or other organizations that handle sensitive customer information.
I think that is all I can think of now, regarding this topic. Hope the information provided will be of valuable help to you.
Until next time, hope you stay safe and secure.
Rewin Koul (rewin-koul.blogspot.in)
To start with, if you want to be completely secure, free from all kinds of threats; the only solution available is to never buy a computer. But you probably already own a computer, so the next option can be to bury it 8 feet under the ground. No other safety measure you take can assure 100% security to you or your online communications. But then, who needs 100% security? Almost all the people using the internet are not preplanned victims, but gullible innocent web browsers that fall prey to shrewd hackers.
To safeguard you from this, almost all the web browsers provide you with some basic security features that you should be aware of while going online, because your privacy is important to you. Here, we discuss about IE, although most of these features are same/similar in all browsers, some browsers support extra features for better security options.
Now, taking IE in perspective let us talk a bit about its essential features which set it apart from other browsers. IE truly provides a hugely rich set of security features that can be configured. Microsoft defines security “zones” such as "Internet," "Local intranet," "Trusted sites," and "Restricted sites." Although each of these categories is fairly loose, each can be finely tuned to suit the user’s needs.?
?In fact, the level of tuning options in IE is almost daunting. Other browsers, say Firefox, which has a powerful but simplistic set of choices. It follows the all- or-nothing principle. Either it can be followed or not, for every site. IE makes it easy to make separate zones for particular websites such that even a lay-man can place sites into the zones based on how much trust it has on the respective website. These settings at first do limit the functionalities for websites that are not added to the “secure zones” and may seem irritating to the user at first, but intrinsically they save us from all scripting attacks and unwanted pop-ups etc. are not displayed on sites that are not in the secure zones.
How to change zones’ settings in IE :
In Internet Explorer, select the "Tools" menu, then "Internet Options". Select the "Security" tab. This will bring up the screen shown to the right. To modify one of the four security "zones", click on the zone's icon, then click the "Custom Level" button.

How to add sites to the secure zone :
To add a site to the "Secure Zone", click on the "Secure Zone" icon in the "Security" tab, then select the "Sites" button. The screen shown on the right will be displayed. Enter the name of the site to add, (including the "http://" bit), then click the "Add" button.

For more control over what features are allowed in the zone, click the Custom Level button. Here you can control the specific security options that apply to the current zone. For example ActiveX can be disabled by selecting Disable for Run ActiveX controls and plug-ins. Default values for the High security setting can be selected by choosing High and clicking the Reset button to apply the changes.

The Privacy tab contains settings for cookies. Cookies are files placed on your computer by various sites that you visit either directly (first-party) or indirectly (third-party). A cookie can contain any type of data. It is often used to track your computer as you move through a web site and store valuable information. I recommend that you select the “Advanced” button and select “Override automatic cookie handling”. Then select Prompt for both first and third-party cookies. This will prompt you each time a site tries to place a cookie on your machine. Also, if the number of cookie prompts are too many and unbearable, the option to “Always allow session cookies” can be enabled.

I would like to mention some other very basic points that would help keep you safe “online”. Be careful only on the pages where you fill some kind of form thereby providing the host with some of your credentials. That is where the hacker actually beats you to collect your information. The most common practice that hackers adopt is to make a ‘Phishing Page’. A phishing page is a web page that looks exactly like a trusted website and sometimes even performs the exactly same desired functionality. It is relatively very easy to detect a phishing page, in case you ever land on one. Always while typing in personal information, take care of the web address, the url. The url can be long and complex and twisted, but it should always start with a fixed format i.e. “www.xyz.com”. Here, “xyz” is the name of the site. This is often modified as www.ab.xyz.com or something similar. What you need to keep in mind is that the word preceding “.com” should be the actual name of the site you need to visit. IE has a built in feature of Domain Highlighting wherein this true name of the website is highlighted in black and the rest is shown in grey. So, its pretty easy to identify a fake page.
Also, IE has Cross site scripting (XSS) filter, which can help prevent attacks from phishing and fraudulent websites that might attempt to steal your personal and financial information. Plus, a 128-bit secure (SSL) connection for using secure websites. This helps Internet Explorer create an encrypted connection with websites run by banks, online stores, medical sites, or other organizations that handle sensitive customer information.
I think that is all I can think of now, regarding this topic. Hope the information provided will be of valuable help to you.
Until next time, hope you stay safe and secure.
Rewin Koul (rewin-koul.blogspot.in)











